Optional but recommended: Instructions how to verify the installer file.
This involves using gpg (get it here for Windows) to input 3 files, and checking a True or False output:
- The data (The installer executable)
- My public key (extracted from my private key – not for you to see ;P)
- My signature (created using my private key and data)
Public Key:
It’s best to find a copy of my public key from a different source (eg a keyserver, GitHub, or my webpage – armantheparman.com. This eliminates the need for you to trust this particular website’s information.
If you have gpg already installed on your computer, you can use this command in the terminal with ‘cmd’, or ‘command prompt’ (that’s the black screen thingy that hackers use):
gpg --keyserver keyserver.ubuntu.com --recv-keys E7C061D4C5E5BC98
If a page opens in your browswer instead of downloading, just right-click and save the file.
You can then import the key to your computers’ key ring (make sure you navigate to the directory where you downloaded the file):
gpg --import parman.asc
The signature
Verify
Then this is the command to verify the file (again, make sure you’re in the right directory):
gpg
--verify
P4Win_v0.0.2.exe.asc
P4Win_v0.0.2.exe
These are basically 4 elements separated by a space (color to help you see):
- The ‘gpg’ program
- The ‘–verify’ option
- The filename of the signature (make sure you’re in the right directory, otherwise you can type the full path to the file beginning with c:\)
- And finally the filename of what you’re verifying.
You should see “Good signature” in the output, and it’s safe to ignore the warning you always get:
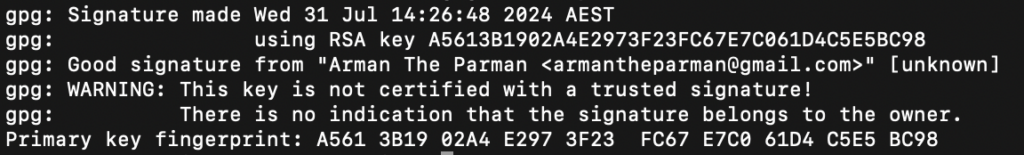
This just means you haven’t fiddled with the settings to tell the computer you trust my public key – the one you carefully found and imported.
Once you get this successful output, you can be sure the exe file you downloaded is identical to the one that I vouched for.